Martijn Grooten - Elliptic Curve Cryptography for those who are afraid of maths
HTML-код
- Опубликовано: 12 июл 2024
- Elliptic Curve Cryptography (ECC) is hot. Far better scalable than traditional encryption, more and more data and networks are being protected using ECC. Not many people know the gory details of ECC though, which given its increasing prevalence is a very bad thing. In this presentation I will turn all members of the audience into ECC experts who will be able to implement the relevant algorithms and also audit existing implementations to find weaknesses or backdoors. Actually, I won't. To fully understand ECC to a point where you could use it in practice, you would need to spend years inside university lecture rooms to study number theory, geometry and software engineering. And then you can probably still be fooled by a backdoored implementation. What I will do, however, is explain the basics of ECC. I'll skip over the gory maths (it will help if you can add up, but that's about the extent of it) and explain how this funny thing referred to as "point addition on curves" can be used to exchange a secret code between two entities over a public connection. I will also explain how the infamous backdoor in Dual_EC_DRGB (a random number generator that uses the same kind of maths) worked. At the end of the presentation, you'll still not be able to find such backdoors yourselves and you probably realise you never will. But you will be able to understand articles about ECC a little better. And, hopefully, you will be convinced it is important that we educate more people to become ECC-experts.
 Наука
Наука
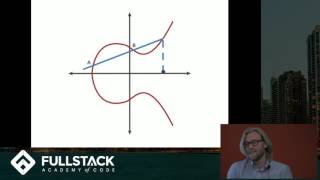








I've watched a number of ecc explanation videos for math novices like myself. This is clearly one of the better ones and one I am much more able to understand. Great job. Thanks so much for sharing!
great speaker, explaining hard concepts in a very friendly way, kudos to him!
Thanks. This is excellent. I had to watch it a few times but I get your explanation. In particular I appreciate your comments on what could go wrong and concerns with NSA.
The Best explanation! Thanks.
I like the speaker, and good explanation.
explained it so well ...
thank you for this persentation
Great talk, thank you.
Great explanation.
15:42 "there are good girls and bad girls"
Of course
Superb Man.... Superb!!!
Thanks, awesome talk! :)
I believe that we should avoid the particular curve which is standard by NIST due to a possible backdoor. But then again how secure are the other curves? Moreover, since there has been questions even on SHA-256, then possibly the bitcoin is in risk.
Nice. Thx
Great decoder
so clearly
Can someone explain me or give more detail on what he says at 20:59 ??
what don't you understand ? it's actually the basic way how random numbers are generated using an EC.
thinking about vector * scala, where the vector is your random bytes array from /dev/random, and the point is an on the curve; even if your random bytes aren't random (assuming they aren't due to NSA shindig) the scala multiplication of your random bytes vector with the point will generate a better random point from the curve since multiplying a point on an EC curve makes it jump around in a seemingly /random/ manner. reversing this is /very/ costly for a CPU, or even a CPU cluster the size of several stadiums.
I understand the spirit of the presentation; but, looks like some confusion between bits and bytes.
I watch this to treat insomnia
mimblewimble!!!
Nice book: Rational points on Elliptic curve, Springer 00:36
"I don't think there is a secret formula for this large number that appears in the standard without explanation." is a pretty useless way of thinking about it.
in ECC , a point on curve is shared between two bodies. How is the message lets say "hello" is encrypted and decrypted using ECC?
wireshark demo: 14:15
still can't understand completely, but I think I got some idea... anyway, give up on understanding this... my math sucks.
Loop in curve 16:07
You believe in what NSA provide? Are you nuts???
so if NSA knows the number d, then why are we using this security crypto?
Thank you Martin for the great presentation. You have nailed the problem very well.
I for one will not use ECC.
Thanks for the kind words. However, please note that I was not saying you shouldn't use ECC, just that you should avoid this particular implementation (and not just because of the NSA backdoor - it's bad for other reasons too).
Hi @@martijngrooten5294 , Could you inform a good and secure curve implementation? What about the secp256k1 used in Bitcoin?