Это видео недоступно.
Сожалеем об этом.
Blockchain tutorial 11: Elliptic Curve key pair generation
HTML-код
- Опубликовано: 9 апр 2017
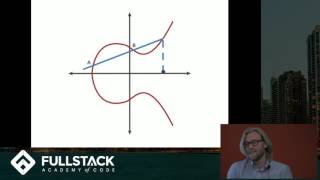
- This is part 11 of the Blockchain tutorial explaining how the generate a public private key using Elliptic Curve.
In this video series different topics will be explained which will help you to understand blockchain.
Bitcoin released as open source software in 2009 is a cryptocurrency invented by Satoshi Nakamoto (unidentified person or group of persons).
After the introduction of Bitcoin many Bitcoin alternatives were created. These alternate cryptocurrencies are called Altcoins (Litecoin, Dodgecoin etc).
Bitcoin's underlying technology is called Blockchain.
The Blockchain is a distributed decentralized incorruptible database (ledger) that records blocks of digital information. Each block contains a timestamp and a link to a previous block.
Soon people realises that there many other use cases where the Blockchain technology can be applied and not just as a cryptocurrency application.
New Blockchain platforms were created based on the Blockchain technology, one of which is called Ethereum.
Ethereum focuses on running programming code, called smart contracts, on any decentralized application.
Using the new Blockchain platforms, Blockchain technology can be used in supply chain management, healthcare, real estate, identity management, voting, internet of things, etcetera, just to name a few.
Today there is a growing interest in Blockchain not only in the financial sector but also in other sectors.
Explaining how Blockchain works is not easy and for many the Blockchain technology remains an elusive concept.
This video series tries to explain Blockchain to a large audience but from the bottom up.
Keywords often used in Blockchain conversation will be explained.
Each Blockchain video is short and to the point.
It is recommended to watch each video sequentially as I may refer to certain Blockchain topics explained earlier.
Check out all my other Blockchain tutorial videos
goo.gl/aMTFHU
Subscribe to my RUclips channel
goo.gl/61NFzK
The presentation used in this video tutorial can be found at:
www.mobilefish.com/developer/b...
The presentation used in this video tutorial can be found at:
www.mobilefish.com/developer/b...
The python script used in the video:
www.mobilefish.com/download/c...
Cryptocurrency address generator and validator:
www.mobilefish.com/services/c...
Desmos graph:
www.desmos.com/calculator/kkj...
James D'Angelo, Bitcoin 101 Elliptic Curve Cryptography Part 4:
• Bitcoin 101 - Elliptic...
#mobilefish #blockchain #bitcoin #cryptocurrency #ethereum








This series is phenomenal! It not only teaches about blockchains, but also teaches, by its example, how to make a RUclips tutorial. You have all my respect and gratitude.
by far the best explanation of EC I've ever seen. Thank you.
This tutorial has saved me from a lot of headaches.
Thank you for your whole series. You have opened my eyes to the world of crypto.
thanks for this videos, i understand the concept with your fast but well explained ideas
Dude you are a king with James D’angelo thank you so much for the value tools 🛠
🙇🏽
Thank you so much to have someone with this level of expertise, who gives up their time to presnt this, is phenomenal . I think a true expert can present extremely difficut concepts in a simple manner, you did this excellently. thanks again
Thankyou for the great videos!
Excellent video. Thank you.
Thank you! very well explained! ✅
Great video to explain ECC
Great explanation, thanks
The best. Thank you.
Bitcoin : "Don't trust verify". Also Bitcoin : Trust the Generator and the parameters given by NIST
Awesome. thanks. great depth on the curve explanation, point or dot addition has nothing to do with regular addition as people would conceive of it. so much in science appears to be needless obfuscation. But I guess people cannot understand what the doctor is saying either, and the doctor cannot understand per se, that they cannot understand per se. Nice job pointing all this out.
EC "doubling" is just a name for a process, not actually doubling
EC "addition" just a name for a process, not actually addition.
Thank u so much.. You r awesome👏✊👍
If P and Q make vertical line, the line intersects the curve at infinity... what? no, the line will never intersect with the curve.
very attractive videos
Great!
I think that only bitcoin geeks can understand this. You are talking about prefixes, RSA etc. Normal people get jam at eliptic curve shape - why like that (some table with values), why to infinity etc. But for geeks it is great.
Great explanation...but i didnt understand the binary representation of public Key, it's based on IEEE 754 format or here you use only integer values ?
Thank you for your clarification. I surfed a bunch of websites and video but can not understand this algorithm.
There is (at least) one point that doesen't intersect the curve, that is when y = 0
Question about the python code example: you use range (1, len(ScalarBin), but it seems this skips over the first bit in the private key. Is this intentional?
a tangent line at the intersection of the curve and the x axis would not intersect the curve again no?
Hi, understanding that this code is originally from James back to 2014, I have a question on line 42: why is it from 1 to 256? I have run this code and found that the iteration in fact only applies on bit 1 to 255 of private key, and therefore the first bit of private key is omitted. Is this the design purpose?
Very good question and to be honest I do not know myself.
I wondered myself a few years ago why this was (..these little nagging questions floating in my head..)
So if anyone know the answer, please let me know, so I can sleep better at night ;-)
Hi, I am also wondering the same thing. The first bit certainly is being skipped, yet the public key provided by the code is correct. I would also like to know if this is by design.
Why does the algorithm double on every bit in the scalar and only adds the original generator point to Q on every bit that equals 1?
From what other ECC explanations have said, the scalar is the number of times the generator point is added to itself (doubled). What it looks like is that the algorithm presented is taking a shortcut to doing this. Can someone explain how that shortcut works?
Classic stuff, when computing nP you do not perform n-1 additions, you use the binary representation of n, when the bit is one you perform an addition and when the bit is 0 you perform a doubling. This is the way we do modular exponentiation i.e. a^b mod (p).
You have to do it that way because if n is huge, say around 2^256, it would take billions of years to compute nP by performing n-1 additions.
Ex1.: 9P is not computed as P+P+P+P+P+P+P+P+P; Since 9 = 2^3+1 = 1001(2) you do 3 doubling and one addition: 2(2(2P)) + P
Ex2.: 524289P is not computed as P+...+P (524288 additions); Since 524289 = 2^19+1 = 10000000000000000001(2) you perform 19 doubling and one addition 524289P = 2(2(2(2(2(2(2(2(2(2(2(2(2(2(2(2(2(2(2P)))))))))))))))))) + P
Following link may be useful (scroll down to right-to-left binary method) en.wikipedia.org/wiki/Modular_exponentiation
Can you teach me how to convert some kind of bit hash to
ripmd160 using a paper and pen
Wouldn't YsubG = (XsubG^3 + 7) ^ 1/2 at the bottom of the slide at 4:55?
You have YsubG = (XsubG + 7) ^ 1/2
But the SecP256k1 has y^2 = x^3 + 7, right?
Yes, you are right. I have made an error in my presentation.
My presentation is based on my web application (where the formula is correct) but I copied the data wrongly.
www.mobilefish.com/services/cryptocurrency/cryptocurrency.html
I will update my presentation. However I will not update my video (too much hassle):
www.mobilefish.com/developer/blockchain/blockchain_quickguide_tutorial.html
No prob.. just wanted to point it out.. surprised nobody else mentioned it.
Thanks for the lecture. :)
i try to calculate it but it wont work, where is my error?
i use python:
x = int("0x79BE667EF9DCBBAC55A06295CE870B07029BFCDB2DCE28D959F2815B16F81798", 16)
y = float.hex((x ** 3 + 7) ** 0.5)
and y is not the uncompressed point, but i wont see my misstake pls help, i also tried y = float.hex((x ** 3 + 7) ** 0.5) % p
with p = 115792089237316195423570985008687907853269984665640564039457584007908834671663
wont work too -.-
@@BinaryZeroTV The square root is meant as a square root in Z/pZ i.e. the square root of a mod p is the x such that x^2 = a mod p. One has to define that more precisely because x^2 = a mod p does not always have a solution and if it has a solution, the solution is not (necessarily) unique.
Example: p = 7, x^2=5 has no solution in Z/7Z, x^2 = 2 has solutions 3 and 4 in Z/7Z.
The following may help you: www.geeksforgeeks.org/find-square-root-modulo-p-set-2-shanks-tonelli-algorithm/
How was the private key generated , was it a random value ? Referring to program example at the end
The private key is random generated, see: www.mobilefish.com/services/cryptocurrency/cryptocurrency.html
Given 𝔽_p {0,…p-1} where p=ℤ modulo 2²⁵⁶-2³²-977, would the curve y² = x³ + 7 even look like the one you showed?
Not sure what your question is:
www.desmos.com/calculator/kkj2efqk5x
Hi. The public key is generated using ECDSA, but is the private key also generated using ECDSA or generated randomly with another algorithm?
It's just a 256 bit cryptography strong random number.
For some reason this code doesnt show the same result in python 3.7 when i swithced bacck to 2.7 i got same results as the author. Why do u think this might happen?
i understand how the public key is calcualted,
but how was the Private Key generated in the first place?
It is random generated, see: www.mobilefish.com/services/cryptocurrency/cryptocurrency.html
Good tutorial, but I don't understand from where you got that private key
Look at this online tool: www.mobilefish.com/services/cryptocurrency/cryptocurrency.html
Transactions Challenge. To set a new record, they used their own software [39] based on the Pollard Kangaroo on 256x NVIDIA Tesla V100
if Y^2 = X^3 + 7, then Y = Sqrt(X^3 + 7) ... so how is YG = ( XG + 7 )^0.5. ????
You are wright. He just forgot to write the exponent "3" of X
Is a link available to your desmos example?
www.mobilefish.com/services/cryptocurrency/cryptocurrency.html
If you all the presentations, see:
www.mobilefish.com/developer/blockchain/blockchain_quickguide_tutorial.html
First thank you for the great videos and material! I didn't find any links to the desmos instance. I realize you've provided all of the supporting math to compute what you did, but I'm not familiar with desmos "the tool" in order to take your material and enter it via it's interface. However I wanted to see the visual relationship between the points that you showed in the video. If it's not possible to share a link to the actual desmos instance I completely understand.
I have updated the description:
The python script used in the video:
www.mobilefish.com/download/cryptocurrency/bitcoin_ec_key_generation.py.txt
Cryptocurrency address generator and validator:
www.mobilefish.com/services/cryptocurrency/cryptocurrency.html
Desmos graph:
www.desmos.com/calculator/kkj2efqk5x
James D'Angelo, Bitcoin 101 Elliptic Curve Cryptography Part 4:
ruclips.net/video/iB3HcPgm_FI/видео.html
Thanks so much!!!
How is the private key generated?
See: www.mobilefish.com/services/cryptocurrency/cryptocurrency.html
Hello, when I execute the algorithm using secp256k1 with the given parameters, the result I got is PublicKey[0] = 0.0 and PublicKey[1] = 0.0 and an error on the number format: "TypeError: %x format: an integer is required, not float".
I'm currently using PyCharm Community Edition to writePython code.
Am I missing something? Can you please advise?
Thank you.
Sorry, I do not know "PyCharm Community Edition ".
The python script works on a Mac using Python 2.7.10
Very different from the typical eliptic curve tutorials. But still seems overwhelming to comprehend. Although your english are not so good it was helpful. But why uncompressed 04 equals 0x in Python?
No, 0x simply denotes a hexadecimal in most languages, like say 0x436174, which is the hexadecimal representation of the word Cat, using the ASCII code. A hexadecimal number padded by 04 would thus start like this: 0x04…
Speak for yourself. His English is great. In all his videos in this series, he is very clear and unambiguous.
Omar Shanti correct. His English is excellent and his videos are excellent.
His English is excellent.
Terrible Dutch accent.