How to use the NIST Cybersecurity Framework
HTML-код
- Опубликовано: 9 июл 2024
- Get the template: youexec.com/presentation-temp...
Table of Contents:
00:00 - Introduction
00:56 - How the NIST framework benefits businesses
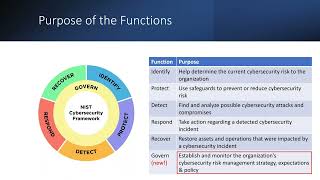
02:06 - What are the key elements of NIST cybersecurity framework?
04:04 - How to show risk analysis findings under NIST
05:05 - How to evaluate cybersecurity maturity with NIST
05:58 - How cybersecurity cost-benefit analysis works under NIST
07:19 - How uptime and downtime monitoring helps to ensure cybersecurity effectiveness
08:07 - Conclusion
Gone are the days when businesses only had to think about bringing in revenue. While growth is always welcomed, businesses also need to focus on reducing disruptions. From systems downtime to loss of critical data, cybersecurity breaches not only interrupt usual operations, but also impact brand reputation and customer trust in the long run. Developed by the National Institute of Standards and Technology, the NIST framework is now widely regarded as the gold standard for cybersecurity posture. When used along risk assessments, cost-benefit analyses, and continuous monitoring, NIST offers the tools for companies to prevent unexpected business interruptions and mitigate financial losses.
Studies show that 65% of consumers lose trust in a company after a data breach, and stock prices can drop by about 5% the day a breach is disclosed. It takes years or even decades of work to build social credibility for a business, and all that can be wiped away in just a few days.
The interconnectedness of today’s business ecosystem proves that cybersecurity efforts shouldn’t be limited to the work of a single department. The NIST cybersecurity framework is particularly useful for bridging the gap between technical and business stakeholders. As a common language and methodology for discussing cybersecurity risks and strategies, the framework allows for better communication, decision-making, and alignment with broader business objectives. This feature sets it apart from other frameworks that may focus solely on technical aspects. Plus, the framework’s flexibility and adaptability is attractive to organizations of all sizes. This allows companies to tailor their cybersecurity programs for their specific needs while staying aligned with regulatory requirements.
To learn more, watch the video in full!  Наука
Наука