How to DECRYPT HTTPS Traffic with Wireshark
HTML-код
- Опубликовано: 1 июн 2024
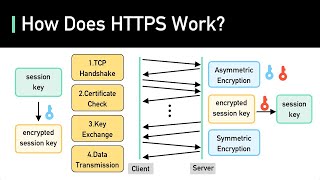
- In this tutorial, we are going to capture the client side session keys by setting an environment variable in Windows, then feed them to Wireshark for TLS 1.3 decryption.
Follow along with me by downloading the trace file and keylog file here:
bit.ly/decrypttraffic
Steps to capture client session key:
Open Control Panel:System
Select Advanced System Settings
Select Environment Variables
Add a new variable: SSLKEYLOG
Save to a location with a name ending in *.log
Restart Chrome (You may have to reboot Windows in some cases)
Capture Traffic
Add the keylog file to the TLS Protocol in Wireshark Preferences.
If you liked this video, I’d really appreciate you giving me a like and subscribing, it helps me a whole lot. Also don't be shy, chat it up in the comments!
== More On-Demand Training from Chris ==
▶Getting Started with Wireshark - bit.ly/udemywireshark
▶Getting Started with Nmap - bit.ly/udemynmap
== Live Wireshark Training ==
▶TCP/IP Deep Dive Analysis with Wireshark - bit.ly/virtualwireshark
== Private Wireshark Training ==
Let's get in touch - packetpioneer.com/product/pri...





![A Day To Remember: Feedback [OFFICIAL VIDEO]](http://i.ytimg.com/vi/iXVnysmQ4e0/mqdefault.jpg)


Thanks as always Chris... really useful 🙏
My pleasure! Thanks for the comment Ganesh!
Even after all the experience I have with IT security/forensics, I’m still learning something new every day.
Amen to that Christopher! I feel the same. I learn something with every pcap I open.
You will always learn something more in technology
'Packet heads' cracked me up. Thanks for the vid!
Glad you liked it! Hey every department needs a Packet Head.
Fantastic guide! I don't normally comment, but you need to know that you are doing fantastic work! I am experiencing Wireshark for the very first time in a CTF and this was clear, informative, and helpful!
Thank you for the comment! I really appreciate the feedback.
Remarkably excellent delivery style. Super efficient clarity. Nothing superfluous. Conceptual through point and click guidance. Compellingly engaging with constant forward quick-step momentum. Not too loud not soft spoken. Knowledgeable, conservative, passionate, trustworthy source. Technoratically enjoyable. First video I watched on this channel. Heading to check your other content for more of the same. Thank you!
Thank you for watching and commenting Alexander!
Chris is a gem...I have learned so much from him over the years, especially on Pluralsight.
Thank you!
Thank you for sharing! Now I can understand ssl/tls handshake clearly and how https works. Love it and Subscribed.
Thanks for the comment!
Thanks Chris. I like your passion when explan all of this. 🤗
Thanks again Di. I appreciate the feedback.
Thanks, Chris. This video helps me a lot.
I just experimented with this in a ucertify virtual lab I had open for a class assignment, and it was super easy and fun. Thank you for showing this !
Great job! Thanks for the feedback!
Thanks, Chris I really appreciate you making videos. Taking the help of your videos I was able to help my colleagues and solve infrastructure problems. Keep making the good stuff as you explain the stuff in quite simple terms.
Nice! That is great Prateek - glad to hear that the videos helped you. More to come!
Thank you so much man. Excellent explanation.
Thank you, Chris, for such a great educational video)
Thank you for this video Chris, I was following the WCNA study guide book but got stuck when I didnt see what's in the book(HTTP). I realised the time gap between the date of book publishing and the current version of wireshark. So switched my trail to 443 and TLS. This video helped me decrypt my session.
Great Samuel! Glad to hear that it helped. I'll get some more TLS 1.3 stuff out there soon.
Can somebody help me?
I am not able to capture the log file even though I created an environment variable with the ssl.log in the end.
finally... a video that works. I can't thank you enough dad.
Thanks grish its really nice and helpful
i havent touched cybersecurity in over a year but bet your ass stumbling on this video made me turn my PC back on, thank you for the insanely ez lesson
Awesome!
Nice to read online that this method apparently works the same with the Firefox web browser :D
Awesome videos. Thank you
You're a God amongst men sir. Thank you
Glad you did the Collab with Bombal so I could find your content!
I am beyond honored that he wanted to interview me on his channel. Great to have you here!
Great video, please keep sharing more
Thanks for the comment! Working on more content and I'll get it out there.
Hi Chris, thanks for this one really learnt a lot here. In saying that I've been seeing more of Application Layer Encryption lately, so in theory if you encrypt at the application level before hitting the pipe and encrypt using TLS, would you be able to get to the cleartext?
Great video and example, thanks for what you do
Thanks for the comment!
A really interesting video indeed!...Learnt many new things....Could you make a video to learn how I can capture and decrypt my smartphone's browsing traffic using wireshark?(Both connected to the same networks)
❤❤It works 💯% dude I don't have a words u are really great!
Thanks Chris. Would you mind sharing the process of path variable for log file in Kali Linux and MAC OS ?
Мужик,лайк тебе ставлю,полезно очень 👍
That’s really interesting!
This is some great stuff, keep going.
Thanks!
Amazing Chris :)
Thanks!
My pleasure!
Thanks Greer, very useful
Thank you Chris!
Thanks you for your great job. I try it and all it works fine!
it means we can decrypt any password even if it uses https protocol ?
Chris, as always you are the man.
@Bill Proctor - Great to see you here Bill! Hope all is well on your end.
@@ChrisGreer absolutely. Just looking forward to being able to travel again for work. Hope to hang out with you sometime soon!
@@grendal1974 That would be awesome Bill! Let's chat sometime here soon.
Thank you so much sir for this wonderful video and it is helpful for us.
Thanks for the comment Tin!
When I saw you change a hat I knew this lesson would be outstanding
Thank you very much Chris 🙏🏻
You are very welcome
Thanks, Chris.
Brilliant!
Great video!
Thanks! Appreciate the comment.
great video. can we decrypt request manually by extracting public certificate of website ?
Cool, thank you!
thanks for the comment Alex!
Wonderful Video 🙏
Glad you enjoyed it!
Great vid, thanks!
Thanks for the comment! I really appreciate the feedback.
@@ChrisGreer didn't know it was that easy. I guess the environment variable you added in the beginning is Chrome specific?
It works with Chrome, Firefox, and some chromium based browsers. I am not much of an Edge user so I haven't tried it myself, and I understand Safari in the Mac environment isn't too happy with this variable either.
Very nice video, TNX.
Thanks!
too cool for a dev, thanks
Great tutorial
Thanks Ginadi. Stick around for more around TLS.
how did u get that SYSLOG file in the beginning?
Don't tell me this isn't the same guy as Darknet Diaries. The voice is IDENTICAL.
Best as always.
Glad you think so!
Thank you.
Hey love the video, how can this be done if I'm not using either chrome or firefox?
Excelent Amigo!
Muchas gracias!
You explain so much more clearly and succinctly than my packet analysis instructor. This is great! Thank you.
Glad it was helpful!
Thank you Sir :)
Most welcome!
You got a new subscriber 🙃😉
Awesome! Thanks for the sub and see you around the channel.
Nice video. Could you do an other video decrypting UDP traffic 🙏 it will help us a lot, thanks
Thanks a lot
Most welcome
Thanks Chris..🙏🙏
Hola, saludos desde Argentina 😃
Gracias por compartir toda esta información.!!
Un placer!
Hey Chris great video!! Any ideas on how we would decrypt https traffic for capture files that are captured in the firewall? In this situation I don’t have the ability to install wireshark in the client machine. Thanks!!
Great video, it´s really useful, thank you!
Hai Chris, how about desktop App not browser, how do we generate that log file?
thank you !
You're welcome!
🔴 Important note the variable name is "SSLKEYLOGFILE" not "SSLKEYLOG" as in the description
Excellent
Thanks doug!
Hi Chris, I have a IOT device connected to AWS. I have all certicates... is it possible to decrypt the communication using wireshark? My IOT device is connected to an access point. Actually, I have a switch that I can route all the traffic to the PC but all packets are encrypted. So, I'd like to see the packet contents. Thanks a lot!
Wait so can I store the keys wherever or does it need to be that specific user address?
Hi Chris, thank you for this very useful information. However, in my current case that got me here, the communication is between two web services which talk to each other via WCF (soap protocol) and i’m in the client side. How to do this if there is no browser involved?
Hello Volkan, I haven't had to do it in that specific environment, so I'm not much help there. Suggest more searches around capturing the keys in that use case. Thanks for the comment.
Very useful, how we can do it on linux with mitm? Hope to see this in the next video
Does this only work with Chrome? Or will it log keys from windows update and other OS calls?
Hi Chris, so sorry, after I tried to save the SSL Key log file, I cannot find the file at all, for some reason. I am the administrator but I just cannot find it. Is there anything I must do? Thanks!
Chris, is there a way to do this in the uplink device? using MITM
hey Chris Greer,
I have done the same as you did even choosing the alphabets same as you did.
No log file is being generated on the folder. restarted chrome/restarted the system but nothing is showing up.
Learn it by heart -- By order of the peaky blinders
Thank you Chris...This is an amazing video...I wanted to know is it possible to do the same with safari browser in Mac os if so can you please point me the steps... Thanks in advance.
Greetings, I would like to know if you can make an intercion video of 2fa or otp by ss7
or if you have some way to do, thanks
Great information 🙂
Please do some video on HTTP3 and its benifits...
Found this channel after watching your colab on David's channel...
Thank you 😊
For sure! I will be doing more content around QUIC and H3 as things continue to develop. Thank you for the comment. I the meantime check out my QUIC decryption video here - ruclips.net/video/QRRHA_5hS2c/видео.html
Hello, was wondering if the decryption could be done using a MITM, for instance the MITM proxy...Would be great to see that happen!!! Ty
Hey, thanks for the comment. I'll see if I can get it working... (or breaking, depending on how you look at it!)
Hello! Good video! I tried to decrypt anything along two days but I haven`t had any success.. I created a system environment variable - there was keys from a browser... What`s going on?
Hi Chris,
In the video, it was told that this is specific to chrome browser. Is it so? Because i did not see any setting which is made specific to store session keys for sessions in chrome browser
I used the chrome browser to demonstrate this in the video, but it also works on Firefox Nightly and I have seen it work on Edge too.
hi I'm from Indonesia ❤️
Thanks for the video. Please could you explain why we see under Transport Layer security TLSv1.3 and the Version TLS 1.2 (0x0303) at 6:47?
Chris, I'm having a strange issue where only about 70% of my TLS traffic is decrypted this way. It seems when using the ECDHE cipher, the packet can't get decrypted even with the master log file. But I'm told the master log file should be enough to decrypt this. Is this true?
I am facing the same issue and currently looking to setup a proxy server like "Charles" but its quiet complicated....
Im so confused. The file that you gave wireshark is completely different from the sslkeylog file that you made earlier. How did you create the file that you gave wireshark?
Hey Josh - I probably had to recreate it and share a different one. However the pcap and syslog you get in the link go together and the rest of the video steps are the same.
Sir appreciate to your work sir I want to ask a question that can we captured username and pass using Wireshark under https trafic
Hello, what wifi adapter are you using for macOS? I want to buy an adapter, but I don't know which one will be compatible with my Mac. Thx)
browser settings can influence packet capture by wireshark? I was trying to test this, but it didn't work, and I thought it might be because of my browser settings.
Please you build on video about how to using the wireshark in windows 10
How do I enable Packet Reassembly and Uncompressed Entity Body?
sir, I have tls.pcap packet , how can i decrypt SIP/TLS v1.2 to see RTP ??
Note that
TLS encrypt by CA ?
You have some really great content on your Channel. You should start accepting BAT's so we can tip you!
Hi Chris D - Thanks for the comment. Actually I had considered setting something like that up but wasn't sure if anyone would actually do it! I appreciate the suggestion and will definitely look into it.
I'm loading the file to Wireshark, but some reason the decryption is not working. I'm using a windows machine.
can you please create a video for decrypting tls traffic in wireshark using private key file
Chris, I was working on tls1.2 SSL client and I try to communicate with webserver. After the application data server throw an error Encrypted Alert 21. Unfortunately I was using DHE key exchange. So i am not able to decrypt the wireshark. Any alternative method is possible? Or i want to know how to decrypt the wireshark while using Diffe hellman key exchange.
about session keys how i could fix that on mac os?
how do you decompress the tls packets though? I want to convert the ascii into plaintext